Locky or Trickbot - Campaign and Infrastructure Analysis
The malicious email contained the base64 encrypted 7z compressed file in the email body! and did not arrive as an attachment. I am unable to comprehend why would the attacker send encoded malicious attachment in email body.

The mail with subject "Supplement payment <somenumber>" was received from an ip assigned to an Indonesian dyndns service provider:
The email domain of the sender was "rec.ca". IBM X-Force Exchange shows the malicious attachments which were sent from this domain
We can see that these are 7z files.
This is the webpage for reg.ca
I copied the base64 encoded hex to a file called "infected_attach" and then decoded it and piped the output to infectedzip.7z file.
we can see that it is indeed a 7-zip archive file:
I moved the decoded 7z file to my lab and found a vbs inside it
Windows Defender identifies the vbs as VBS/Schopets
Hash of the vbs 57030ddd567e2bc26e75ef8ac2359079
Strangely VT had 0 detection for this vbs
I proceeded to debug the script using Visual Studio:
Pirates :)
User Agent which is used by this malicious vba to communicate with:
1. Download sites hosting the malware
2. C2 communication
We can see the name of the exe, which will be written on disk
We can see Microsoft.XMLHTTP object being created
and Adodb.Stream as well.
Also There is usage of Ref() function, which does not make sense here as the script is not running in the context of a webpage
Here it is checking if the current script is running in the context of "Windows Script Host":
Getting the Process Env Variables
Getting the Temp env variable value
Some of the developer’s statements are commented hinting on what he might be upto when writing this.
The interesting part is here where the script detects the country where the victim is located. It is using free APIs by freegeoip, geplugin and ipinfo for this purpose.
We can also see an array of country codes (GB=United Kingdom, UK=Ukraine, AU=Australia, LU=Luxembourg, BE=Belgium and IE=Ireland)
We can see result of all of the three services:
We can see the User string value:
Once the script gets the response from geolocation API, it parses it and look for the country code:
Next the script checks whether the country code given by the response equals the above mentioned country codes, if yes then the first set of URLs will be used to download the malware, In case the country is different than the above 6 countries then a different set of URLs will be used to download a different malware:
In any case the malware was no long available as we could see 404 response. However, I was able to get the samples from somewhere else.
The script also uses WMI query to get information of countrycode, version of OS and OStype:
we can see the concatenated string comprising of the information collected:
This information is POSTed to the C2 server
The complete request can be seen below:
Lots of Unused
code
Why is this interesting to me. Because the unused code if written or borrowed by the malware author, would indicate his/her interests, maybe a code collection could indicate projects he/she has worked on, and give some insight on the mindset of the threat actor:
Next, I started looking up the snippet of the above unused code on both conventional as well as dark web:
Using strings (unused code), I discovered earliest samples
of the same campaign (similar string in vbs files) seen uploaded to hybrid
analysis, Cuckoo, pastebin and others on Sep 4th, 8th, 26,
27, 28, 29 and early October:
- http://cuckoo.cert.ee/analysis/1091724/static/
- https://www.hybrid-analysis.com/sample/899bc84f2d9a752d41e8b9f8b274c9d4d60e709a530b4d065ac68ec53461763c?environmentId=100
- https://www.hybrid-analysis.com/sample/bd9e641e21e52549ea2c0c3ac594ca5b6b00f08bba40cd2a8473e9c53aa08cb7?environmentId=100
- https://www.reverse.it/sample/7b1ffca00cc967596dee82fab700df332bcc5d6999f94abadb82ab2365a9dfbf?environmentId=100
- https://www.hybrid-analysis.com/sample/786bbc27afeb35dd65cbf4469dbbc4d214902538c23d493f709e5fc32f88728e?environmentId=100
- https://www.hybrid-analysis.com/sample/d8b41cb4261cf98024cecc4c2a175199f737ed206218caf3685e09abdde0a4d0?environmentId=100
- https://pastebin.com/Bypn8FEb
- http://mlwr.ee/analysis/997642/static/
- https://pastebin.com/m0LdaahM
- https://pastebin.com/ij2f1S5P
- https://www.hybrid-analysis.com/sample/bd9e641e21e52549ea2c0c3ac594ca5b6b00f08bba40cd2a8473e9c53aa08cb7?environmentId=100
- https://infosec.cert-pa.it/analyze/3134ff6529ef055b232452e3f29bdece.html (Sep 4th)
- https://www.hybrid-analysis.com/sample/f761ec9b9a5b4cc93193ebe78fd9674d2ce3b4b7220e972bf106429f5906f90b?environmentId=100 (Sep 8th)
- https://www.hybrid-analysis.com/sample/29cca7cef6ffbe72e8bef0217fdb9878bee8a808d7fe5782d8139c37d156c780/?environmentId=100
Following domains were contacted by the above samples for
downloading malware:
·
qxr33qxr(dot)com/nui76tg7?
·
Nsaflow(dot)info/p66/nui76tg7
·
yamanashi-jyujin(dot)jp/nui76tg7?
·
Miamirecyclecenters(dot)com/09yhb7r5e?
·
Nsaflow(dot)info/p66/09yhb7r5e
·
Atlantarecyclingcenters(dot)com/09yhb7r5e?
·
autoecolejeanluc(dot)com
·
associationlachaloupe(dot)com
·
poemsan(dot)info
·
foxcabinets(dot)com/tfhytdrf56u?
·
derainlay(dot)info/p66/tfhytdrf56u
·
mautau(dot)it/tfhytdrf56u?
·
mastertenniscoach(dot)com/iugftrs2?
·
Nsaflow(dot)info/p66/iugftrs2
·
Xploramail(dot)com/iugftrs2?
·
Gandmco(dot)com/9ghf45jhg?
·
Hutterstock(dot)org/p66/9ghf45jhg
·
www.pizzelli(dot)eu/9ghf45jhg?
·
Ernestoangiolini(dot)com/9ghf45jhg?
·
Hutterstock(dot)org/p66/9ghf45jhg
·
gandmco(dot)com/9ghf45jhg?
·
Anderlaw(dot)com/jhdsgvc74?
·
Ideathlike(dot)net/p66/jhdsgvc74
·
arc-conduite(dot)com/jhdsgvc74?
·
Formareal(dot)com/jkhguygv73?
·
Playbrief(dot)info/p66/jkhguygv73
·
fianceevisa101(dot)com/jkhguygv73?
·
Richarddrakeconstruction(dot)com/jhdgc62?
·
Sherylbro(dot)net/p66/jhdgc62
·
Centurythis(dot)com/jhdgc62?
·
Asecontrids(dot)com/d8743fgh?
·
Poemsan(dot)info/p66/d8743fgh
·
Consultingfranquean(dot)com/d8743fgh?
·
Fmarson(dot)com/jkhguygv73?
·
Playbrief(dot)info/p66/jkhguygv73
·
gaestehaus-im-vogelsang(dot)de/jkhguygv73?
·
hxxp://animatoon.be/JIKJHgft
·
hxxp://autoecoleautonome.com/JIKJHgft
·
hxxp://brownpa.net/JIKJHgft
·
hxxp://calpadia.co.id/JIKJHgft
·
hxxp://clubdeautores.es/JIKJHgft
·
hxxp://cogerea.net/JIKJHgft
·
hxxp://dueeffepromotion.com/JIKJHgft
·
hxxp://hard-grooves.com/JIKJHgft
·
hxxp://hellonwheelsthemovie.com/JIKJHgft
·
hxxp://prescottinternet.net/JIKJHgft
·
hxxp://qxr33qxr.com/JIKJHgft
·
hxxp://suncoastot.com/JIKJHgft
·
hxxp://uvitacr.com/JIKJHgft
·
hxxp://www.pentahealthinstitute.com/JIKJHgft
·
hxxp://naturofind.org/p66/JIKJHgft
·
babyemozioni(dot)it/KJSkjdhf?
·
Tertrodefordown(dot)info/af/KJSkjdhf
·
baptistown-nj(dot)com/KJSkjdhf?
And the IOCs from the sample I was analysing:
Malware Download Domains
For GB UK AU LU BE IE
·
Highlandfamily(dot)org/jhbfvg7?
·
Fetchstats(dot)net/p66/jhbfvg7
·
bnphealthcare(dot)com/jhbfvg7?
For rest
·
team-bobcat(dot)org/8y6ghhfg?
·
Fetchstats(dot)net/p66/8y6ghhfg
·
highpressurewelding(dot)co.uk/8y6ghhfg?
C2 Domains
hxxp://unhanorarse(dot)info/tr554.php
hxxp://haddownding(dot)net/trtrtr.php
hxxp://rateventrithathen(dot)info/tr554.php
I proceeded to look up the unused string code further, out of curiosity and to see where would it take me.
Strings from Unused Code, Researched
using OSINT
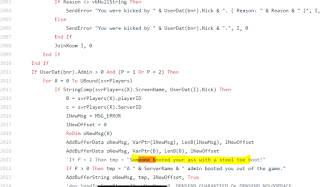
Keyword: "Someone botted your ass
with a steel boot"
A phrase in the unused
code “Someone
booted your ass with a steel toe boot” in the
vbs was also discovered in the following code in a github repo along with
matching unused code in the vb script
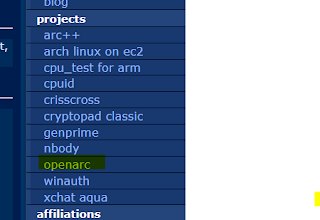
The user is tycho and the
project is called “openarc-vb”.
This is the website of the user tycho
I clicked on the link to projects on the right side
I was directed to the openarc project page in Sourceforge
OpenArc is a Visual basic based project and a clone of "Sierra Arc" project, which is a CTF game (http://openarc.sourceforge.net/index.php?page=about). Sierra Arc was developed in 1997 by John Vechey.
And it seemed that a large portion of code from the project file CobaltServ_modMain.bas was placed in the script. What does this mean? I think the malicious script author might have been working on the openarc project locally on his/her machine, or maybe he/she randomly browsed VB projects on github/sourceforge and copied random pieces of code (subs/functions) and pasted in the script? Maybe the threat actor has some link or interest in the project. Maybe the threat actor is into online games etc.
Keyword: GetShitList(
Next string “GetShitList(ByVal” was found along with matching code in this
repo and in the file modCommands.bas:
Also a VB6 project and a chat bot (Official Site: http://www.stealthbot.net).
The user is called stealthbot and he/she seem to be maintaining the code (last commit May 5th 2017). The user calls himself "Andy T" from Milwaukee, Wisconsin USA:
But I found
something more looking for this same string.
Check this out http://z14.invisionfree.com/Trotup/ar/t3.htm
User = Trotup
User Trotup was also into hacking
When I visited user Trotup’s main page.
It had link to stealthbot forum page also referred by Andy T in his github repo
(user stealthbot). Maybe it is the same person:
Keyword: IsCircleAnalytic
Found the exact code on this site:
https://www.bvbcode.com/code/z0mc6sij-2316994 (signed by Wosign, a chinese CA)
This seems to be a VB project written for "Silverlight online geometric drawing"
I also found this same code uploaded to https://www.ecsdn.com/d-4Kzt.html by user snipernice
This is the homepage of snipernice and it seems to be a Chinese person:
Keyword:LenB(BotVars.BotOwner
Found some reference to this code also in git repo of
Stealthbot
Keyword: "Encryption.Decryptstring(tmp"
Found reference again in the openarc-vb project:
Keyword:
“GetVolumeInformation(strDrive, Drive_Label”
Ref found:
Again found on
https://github.com/tycho/openarc-vb/blob/master/src/Cobalt/CobaltServ_modMain.bas
http://forum.html.it/forum/showthread/t-366079.html (xegallo)
Looking at what gets downloaded
Now let us look at what are the two different hashes, which gets downloaded
Comparing this with the code we have seen that if is either "GB", "UK", "AU", "LU", "BE", "IE"
it would have downloaded and executed
MD5: dbc0aa7e70df7e27ae9169ae0962e2cf
(TrickBot)
Compilation Timestamp
2016-07-03 15:46:13
Creation Time
2016-07-03 15:46:13
First Seen In The Wild
2010-11-20 23:29:33
First Submission
2017-10-11
13:09:22
Last Submission
2017-10-12
19:21:10
Last Analysis
2017-10-20 01:49:54
Otherwise for all other countries it would have downloaded and executed:
MD5: dda37961870ce079defbf185eeeef905
(Locky)
Compilation Timestamp
2016-03-30 00:00:03
Creation Time
2016-03-30 00:00:03
First Seen In The Wild
2017-10-11 11:57:56
First Submission
2017-10-11
12:05:19
Last Submission
2017-10-19
20:38:07
Last Analysis
2017-10-20
05:01:32
The pipes connected to indicates that it is a ransomware
For locky I downloaded the ransomware note in html from hybrid analysis
This is the instructions site in dark web
g46mbrrzpfszonuk(dot)onion/5DYGW69IP3PQSSYC. And we can see the Bitcoin address:
Bitcoin address: 1LkbVYuLXwnJniQj8zHLT4vuqrNHfnMXb8
No payments made yet:
Let us have a look at the malicious domains
First I copied all download URIs and C2 domains, I discovered during my sample collection (see above), to a file “domains.txt”
Then I run the following replacement to get only domain
names and I pipe output to another file “refined_domains.txt”
cat domains.txt | sed 's/•//g' | sed 's/hxxp:\/\///g' | sed
's/www\.//g' | sed 's/(dot)/\./g' | sed 's/\s//g' | sed 's/\/.*//g' >
refined_domains.txt
Next Download Passivetotal python client for querying the
OSCTI source PassiveTotal from RiskIQ
Follow documentation to install
Querying one of the malware download domains results in
default output in JSON
Since I ran out of quota for the PassiveTotal, I decided to
use another service http://whoiz.herokuapp.com/
Simple script to run through the refined_domains.txt file
and get whois info
-----------------------------------------------------Code
Begin-------------------------------------------
import
fileinput
import
os
refined_file
= open("refined_domains.txt","r")
os.system("rm
-f whois_output.txt")
for
aline in refined_file.readlines():
cmd="curl -s
http://whoiz.herokuapp.com/lookup.json?url=" + aline.strip() + " |
grep -i 'domain\|created_on\|updated_on\|organization\|email\|name\|telephone\|url\|city\|state\|country\|country_code\|phone\|fax\|status'
| grep -i -v 'disclaimer\|domain_id\|AFILIAS\|Xferd\Dload' | sed 's/^/" +
aline.strip()+ " /' >>
whois_output.txt"
os.system(cmd)
refined_file.close()
-----------------------------------------------------Code
End-------------------------------------------
The output file looks like this
Domains clustered
with same name servers
arc-conduite.com "name":
"a.dns.gandi.net",
associationlachaloupe.com "name":
"a.dns.gandi.net",
autoecoleautonome.com "name":
"a.dns.gandi.net",
autoecolejeanluc.com "name":
"a.dns.gandi.net",
Anderlaw.com "name":
"dns1.name-services.com",
Atlantarecyclingcenters.com "name": "dns1.name-services.com",
Centurythis.com "name":
"dns1.name-services.com",
foxcabinets.com "name":
"dns1.name-services.com",
gandmco.com "name":
"dns1.name-services.com",
Gandmco.com "name":
"dns1.name-services.com",
Miamirecyclecenters.com "name":
"dns1.name-services.com",
suncoastot.com "name":
"dns1.name-services.com",
hard-grooves.com "name":
"dns1.siteturn.com",
hellonwheelsthemovie.com "name":
"dns1.siteturn.com",
Fmarson.com "name": "dns2.host-redirect.com",
Anderlaw.com "name":
"dns2.name-services.com",
Atlantarecyclingcenters.com "name":
"dns2.name-services.com",
Centurythis.com "name":
"dns2.name-services.com",
foxcabinets.com "name":
"dns2.name-services.com",
gandmco.com "name":
"dns2.name-services.com",
Gandmco.com "name":
"dns2.name-services.com",
Miamirecyclecenters.com "name":
"dns2.name-services.com",
suncoastot.com "name":
"dns2.name-services.com",
hard-grooves.com "name": "dns2.siteturn.com",
Anderlaw.com "name":
"dns3.name-services.com",
Atlantarecyclingcenters.com "name":
"dns3.name-services.com",
Centurythis.com "name":
"dns3.name-services.com",
foxcabinets.com "name":
"dns3.name-services.com",
gandmco.com "name":
"dns3.name-services.com",
Gandmco.com "name":
"dns3.name-services.com",
Miamirecyclecenters.com "name":
"dns3.name-services.com",
suncoastot.com "name":
"dns3.name-services.com",
Ideathlike.net "name": "ns1.texneed.ru",
Sherylbro.net "name":
"ns1.texneed.ru",
dueeffepromotion.com "name":
"ns2.mdsnet.it",
mautau.it "name":
"ns2.mdsnet.it",
brownpa.net "name": "Tucows Domains
Inc.",
hard-grooves.com "name": "Tucows Domains
Inc.",
hellonwheelsthemovie.com "name": "Tucows Domains
Inc.",
qxr33qxr.com "name": "Tucows Domains
Inc.",
qxr33qxr.com "name": "Tucows Domains
Inc.",
Richarddrakeconstruction.com "name": "Tucows Domains
Inc.",
Sorting by
Organization. We can see domains clustered with same organization names
faisal@siftworkstation:/home/sansforensics/incidents$
cat whois_output.txt | grep -i "organization" | sort -k2 -k1
Ernestoangiolini.com "organization": "Ascio
Technologies, Inc. Danmark - Filial af Ascio technologies, Inc. USA",
babyemozioni.it "organization": "Aziende
Italia s.r.l.",
Asecontrids.com "organization": "CCI REG
S.A.",
babyemozioni.it "organization": "Cinzia
Cazzaro",
babyemozioni.it "organization": "Cinzia
Cazzaro",
bnphealthcare.com "organization": "Deluxe
Small Business Sales, Inc. d/b/a Aplus.net",
Anderlaw.com "organization": "eNom,
Inc.",
Atlantarecyclingcenters.com "organization": "eNom,
Inc.",
Centurythis.com "organization": "eNom,
Inc.",
dueeffepromotion.com "organization": "eNom,
Inc.",
fianceevisa101.com "organization": "eNom,
Inc.",
Fmarson.com "organization": "eNom,
Inc.",
Formareal.com "organization": "eNom,
Inc.",
foxcabinets.com "organization": "eNom,
Inc.",
gandmco.com "organization": "eNom,
Inc.",
Gandmco.com "organization": "eNom,
Inc.",
Miamirecyclecenters.com "organization": "eNom,
Inc.",
suncoastot.com "organization": "eNom,
Inc.",
uvitacr.com "organization": "eNom,
Inc.",
Fetchstats.net "organization": "Eranet
International Limited",
Fetchstats.net "organization": "Eranet
International Limited",
haddownding.net "organization": "Eranet
International Limited",
Ideathlike.net "organization": "Eranet
International Limited",
Sherylbro.net "organization": "Eranet
International Limited",
arc-conduite.com "organization": "Gandi
SAS",
associationlachaloupe.com "organization": "Gandi
SAS",
autoecoleautonome.com "organization": "Gandi
SAS",
autoecolejeanluc.com "organization": "Gandi
SAS",
cogerea.net "organization": "Gandi
SAS",
baptistown-nj.com "organization":
"GoDaddy.com, LLC",
mastertenniscoach.com "organization":
"GoDaddy.com, LLC",
pentahealthinstitute.com "organization":
"GoDaddy.com, LLC",
prescottinternet.net "organization":
"GoDaddy.com, LLC",
babyemozioni.it "organization": "Gruppo
Barichello srl",
mautau.it "organization": "Mautau
S.r.l.",
mautau.it "organization": "Mds Net
s.r.l.",
mautau.it "organization": null,
mautau.it "organization": null,
Consultingfranquean.com "organization": "OVH",
gaestehaus-im-vogelsang.de "organization":
"Red-Pearl-Media",
gaestehaus-im-vogelsang.de "organization":
"Red-Pearl-Media",
Xploramail.com "organization": "Soluciones
Corporativas IP, SL",
brownpa.net "organization": "Tucows
Domains Inc.",
hard-grooves.com "organization": "Tucows
Domains Inc.",
hellonwheelsthemovie.com "organization": "Tucows
Domains Inc.",
qxr33qxr.com "organization": "Tucows
Domains Inc.",
qxr33qxr.com "organization": "Tucows
Domains Inc.",
Richarddrakeconstruction.com "organization": "Tucows
Domains Inc.",
Now let us see the updated_date for
domains and we can see clustered domain
updates.
gaestehaus-im-vogelsang.de "updated_on":
"2010-04-28T18:26:37+02:00"
mautau.it "updated_on": "2010-05-04
10:38:26 +0000"
mautau.it "updated_on": "2010-05-04
10:38:49 +0000"
mautau.it "updated_on": "2010-05-04
10:38:49 +0000"
gaestehaus-im-vogelsang.de "updated_on": "2011-02-14
18:01:33 +0000",
babyemozioni.it "updated_on": "2012-02-02
13:45:00 +0000"
prescottinternet.net "updated_on": "2016-09-22
21:09:34 UTC",
yamanashi-jyujin.jp "updated_on": "2016-12-01
01:05:09 +0000",
Consultingfranquean.com "updated_on": "2016-12-29
18:00:48 UTC",
associationlachaloupe.com "updated_on": "2017-02-09
08:01:40 UTC",
arc-conduite.com "updated_on": "2017-02-15
10:28:04 UTC",
autoecoleautonome.com "updated_on": "2017-02-22
15:24:21 UTC",
babyemozioni.it "updated_on": "2017-02-24
01:01:26 +0000",
qxr33qxr.com "updated_on": "2017-02-25
09:03:06 UTC",
qxr33qxr.com "updated_on": "2017-02-25
09:03:06 UTC",
Miamirecyclecenters.com "updated_on": "2017-03-02
11:05:54 UTC",
Atlantarecyclingcenters.com "updated_on": "2017-03-02
11:05:55 UTC",
dueeffepromotion.com "updated_on": "2017-03-03
21:48:08 UTC",
foxcabinets.com "updated_on": "2017-03-05
06:18:18 UTC",
uvitacr.com "updated_on": "2017-03-09
05:09:49 UTC",
pentahealthinstitute.com "updated_on": "2017-03-23
14:26:54 UTC",
brownpa.net "updated_on": "2017-04-03
18:17:26 UTC",
Formareal.com "updated_on": "2017-05-03
10:31:05 UTC",
bnphealthcare.com "updated_on": "2017-05-08
02:59:21 UTC",
hellonwheelsthemovie.com "updated_on": "2017-05-15
19:59:26 UTC",
gandmco.com "updated_on": "2017-05-18
07:54:27 UTC",
Gandmco.com "updated_on": "2017-05-18
07:54:27 UTC",
Richarddrakeconstruction.com "updated_on": "2017-05-19
15:14:53 UTC",
fianceevisa101.com "updated_on": "2017-05-22
17:40:48 UTC",
Fmarson.com "updated_on": "2017-05-23
02:59:40 UTC",
mastertenniscoach.com "updated_on": "2017-06-04
19:17:30 UTC",
Xploramail.com "updated_on": "2017-06-15
13:36:45 UTC",
baptistown-nj.com "updated_on": "2017-06-27
10:53:57 UTC",
autoecolejeanluc.com "updated_on": "2017-07-11
11:48:45 UTC",
Centurythis.com "updated_on": "2017-08-11
08:35:41 UTC",
Ernestoangiolini.com "updated_on": "2017-08-28
07:17:17 UTC",
Asecontrids.com "updated_on": "2017-08-28
20:17:03 UTC",
cogerea.net "updated_on": "2017-09-15
09:13:40 UTC",
hard-grooves.com "updated_on": "2017-09-19
16:43:07 UTC",
Ideathlike.net "updated_on": "2017-09-25
07:46:07 UTC",
Sherylbro.net "updated_on": "2017-10-08
03:00:52 UTC",
Fetchstats.net "updated_on": "2017-10-10
09:53:25 UTC",
Fetchstats.net "updated_on": "2017-10-10
09:53:25 UTC",
Anderlaw.com "updated_on": "2017-10-11
15:23:47 UTC",
suncoastot.com "updated_on": "2017-10-13
23:16:48 UTC",
haddownding.net "updated_on": "2017-10-19
02:45:30 UTC",
mautau.it "updated_on": "2017-10-20
11:35:18 +0000",
babyemozioni.it "updated_on": null
babyemozioni.it "updated_on": null
animatoon.be "updated_on": null,
calpadia.co.id "updated_on": null,
Highlandfamily.org "updated_on": null,
highpressurewelding.co.uk "updated_on": null,
Hutterstock.org "updated_on": null,
Hutterstock.org "updated_on": null,
naturofind.org "updated_on": null,
pizzelli.eu "updated_on": null,
team-bobcat.org "updated_on": null,
These seem to be ads in Japanese
The above link to a PDF document on the domain mautau(dot)it, redirects to http://wrcchq(dot)org/Bank/Scans385.zip. This compressed file is reported to also contain a malicious script, which downloads Locky.
Ref: https://vorsicht-email.de/beitrag/2017/09/27/ups-ship-notification-tracking-number-1z67082y5658349975-von-ups-quantum-view-pkginfo84ups-com/
Ref: http://www.fortiguard.com/encyclopedia/virus/7521270/w32-kryptik-fxnh-tr
Domain: pizzelli(dot)eu
Domain: anderlaw(dot)com
Again we see that the following link on the dueeffepromotion(dot)com domain, redirects to the same URL http://wrcchq(dot)org/Bank/Scans385.zip
Domain: qxr33qxr(dot)com
Another interesting link on this domain qxr33qxr(dot)com. Most probably a concatenation of download links for malware:
dda37961870ce079defbf185eeeef905 (locky)
lodctr /m
/7\uqSFVW
j2rlN8r
T@_W$0A@@AT
delmodem.exe
tmdmnt.sys
_L0ckW0O0B0
dbc0aa7e70df7e27ae9169ae0962e2cf (trickbot)
accc__o_es_Memory
abkke__2_dll
gcai0oQHed
[#zhmibYKtM










































































Comments
Post a Comment