PebbleDash - Lazarus / HiddenCobra RAT
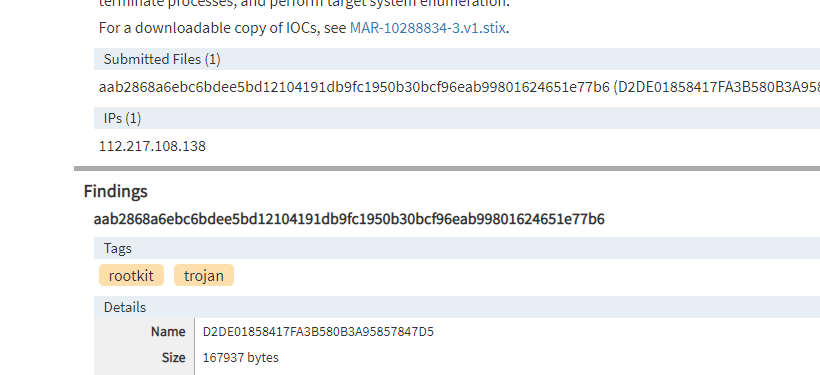
Hi folks. I was analyzing the PebbleDash malware used by Lazarus APT group. While analyzing the original sample (Md5: d2de01858417fa3b580b3a95857847d5), I was able to find out the C2 server and the port, where it intends to communicate to. I also found an interesting technique it uses to identify the OS version of the victim machine.
The sample loads several libraries dynamically during run time. This also included wsock32.dll. Malware usually does this as an anti-analysis technique (anti static analysis)
It then tries to open a socket connection by calling the connect function.

During static analysis, I observed interesting strings were starting with "Zip-bug", as can be seen below. Using yara rules I was able to discover some other samples uploaded to HA (Hybrid Analysis) with the same strings embedded. These samples seemed to be not related to d2de01858417fa3b580b3a95857847d5. However, they communicated to South Korea and China.
While performing dynamic anlaysis, I observed that the sample uses the API call IsProcessorFeaturePresent to determine the version of the victim OS. The
PF_FLOATING_POINT_PRECISION_ERRATA feature is explicitly set to FALSE in x86 version
6.1 and higher.
After loading the libraries the malware saves the memory offset of the API functions it intends to use as can be seen below.
I decoded the "sockaddr" structure which is passed on to the connect function.
The first two bytes in the structure represents the destination port and we can see that it is 443 in this case.
The rest of the four bytes are: 0x70 0xd9 0x6C 0x8A, which translates to 112.217.108.138 (hex to decimal). This is the C2 ip address where PebbleDash communicates to. This IOC also be seen in the US-CERT advisroy.
PebbleDash inserts fake "server name" in the TLS packet. We can see below some:









Comments
Post a Comment