Macros based Downloaders on the Rise
Recently I have come across email with infected macro attachments, bypassing security mechanisms in place by obfuscating the vb code. One such example was a downloader which was discovered .
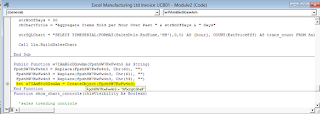
The macro is triggered the autoopen() function which in turns seems to call a randomly generated function xbxGk5Ux3irM4d. Such function names are indicative of a code generator which generates the code automatically.
Secondly some anti analysis techniques were observed again with obfuscated function calls.
After the function call, some other anti analysis techniques were observed where the characters were obfuscated using ASCII values. As it can be seen that further obfuscation is done by putting in between backslashes in the URL, which is removed by subsequent Replace function.
The downloader seem to be downloading a binary bbw.exe
(Hash: da8a659d8ac0a75e0c6936b31331796b) Virustotal did not give any result
The macro is triggered the autoopen() function which in turns seems to call a randomly generated function xbxGk5Ux3irM4d. Such function names are indicative of a code generator which generates the code automatically.
Secondly some anti analysis techniques were observed again with obfuscated function calls.
After the function call, some other anti analysis techniques were observed where the characters were obfuscated using ASCII values. As it can be seen that further obfuscation is done by putting in between backslashes in the URL, which is removed by subsequent Replace function.
The downloader seem to be downloading a binary bbw.exe
(Hash: da8a659d8ac0a75e0c6936b31331796b) Virustotal did not give any result
Microsoft.XMLHTTP is being used by the dropper and Wscript.Shell() is used to execute the malicious binary:
The binary is copied to the the Appdata/Tmp folder with another name "mikapolne.exe":
In the next blog post I will be sharing the analysis of the second stage of the attack by analyzing the downloaded binary.






Comments
Post a Comment